MITRE & The Cyber Kill Chain
https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
https://mitre-attack.github.io/attack-navigator/
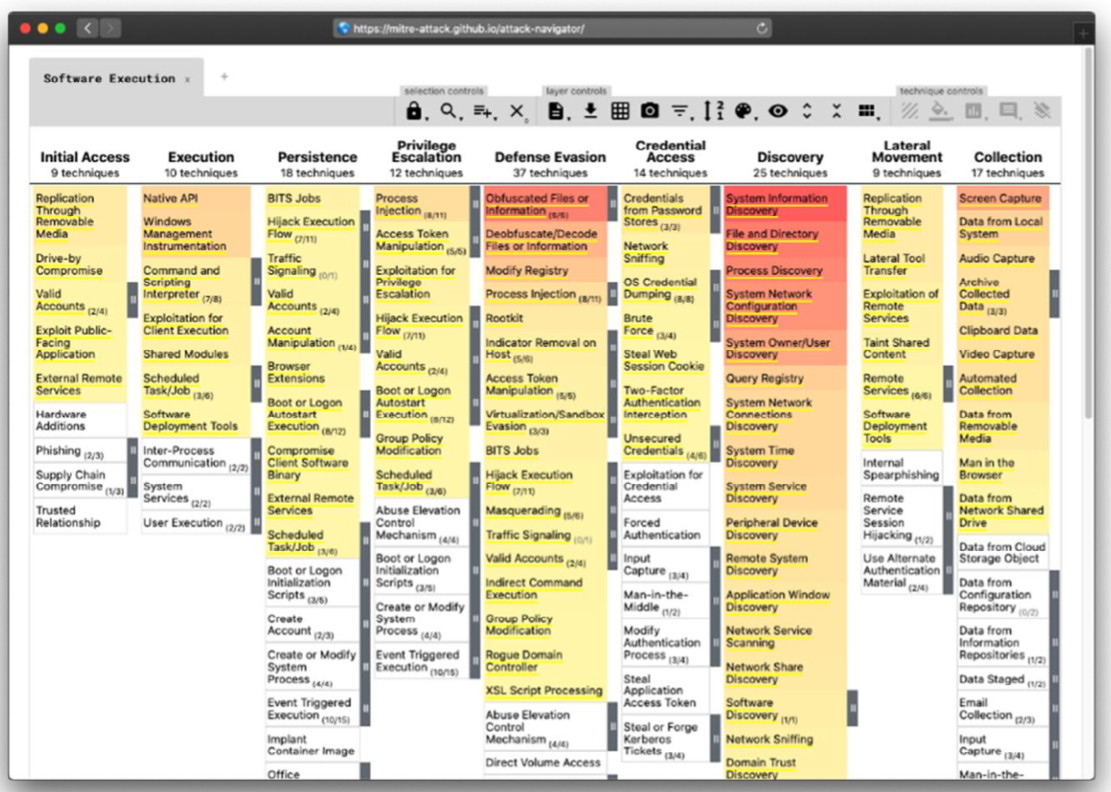
Initial access

Lateral movement
- First, the attacker gains control of a local user
- Then, escalates to local admin
- Then, moves to the AD (domain admin)
- Then, moves to any computer in the network
Exfiltration / Impact
Defenses
A change in paradigm
- 10 years ago: protection. Filter, patch, block
- Currently: detection. Log, alert, react
Results of the Pwn2Own hacking contest: https://therecord.media/windows-10-ios-15-ubuntu-chrome-fall-at-chinas-tianfu-hacking-contest/
All systems are vulnerable
How to protect an endpoint?
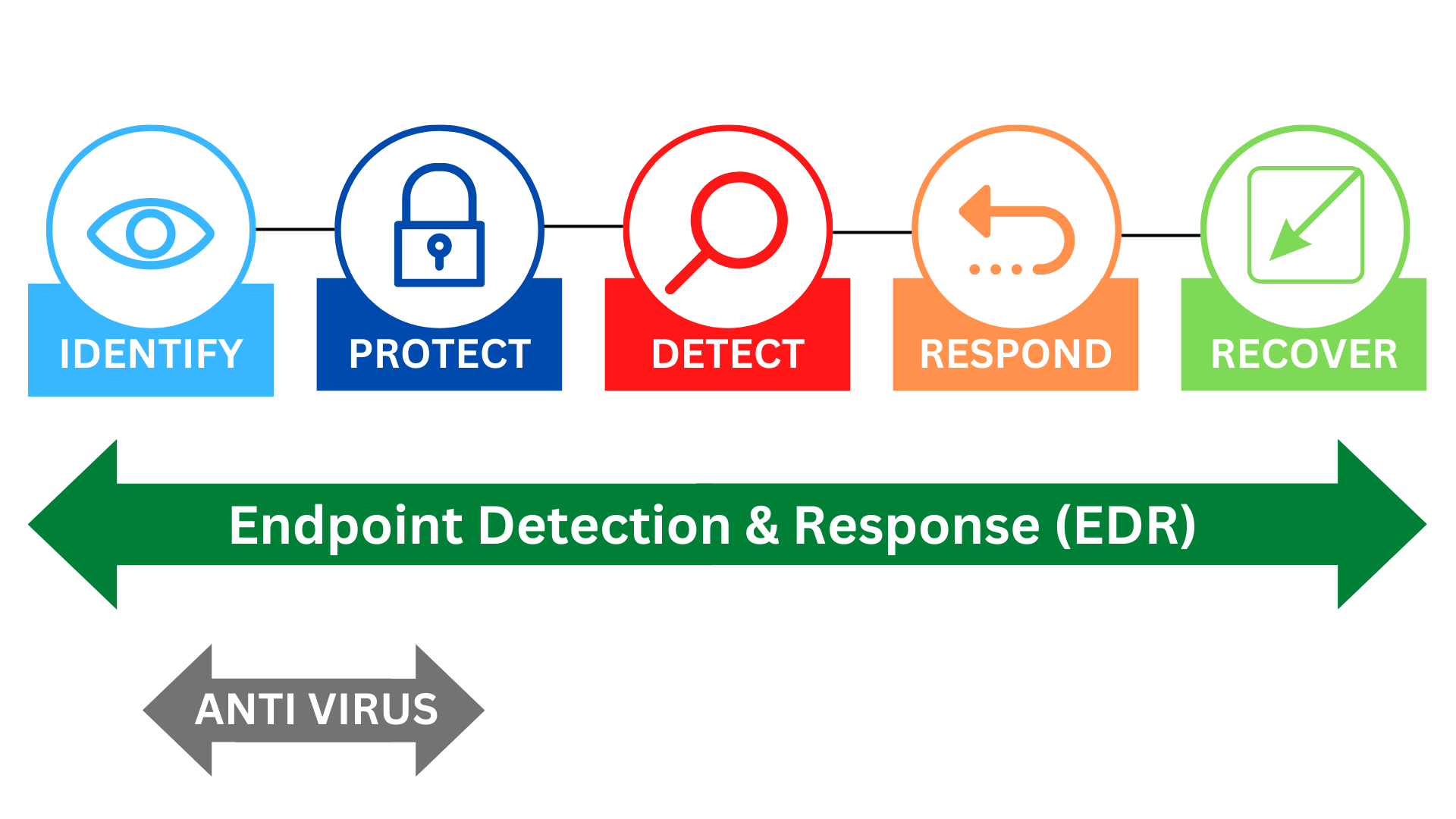
- Default system tools
- Enhanced system tools
- Antivirus
- Endpoint detection and response (EDR)
Sources of information
- System logs
- Linux:
/var/log - Windows: Event Viewer
- Linux:
- System configuration
- Linux:
/etc - Windows: System registry
- Linux:
- System cache:
- Linux:
/tmp - Windows: prefetch, amcache, temp files...
- Linux:
- Application logs
- Linux
/var/log/APPLICATION - Windows: ?
- Linux
- RAM, filesystem...
https://www.sans.org/blog/new-windows-forensics-evidence-of-poster-released/
Windows: Event Viewer
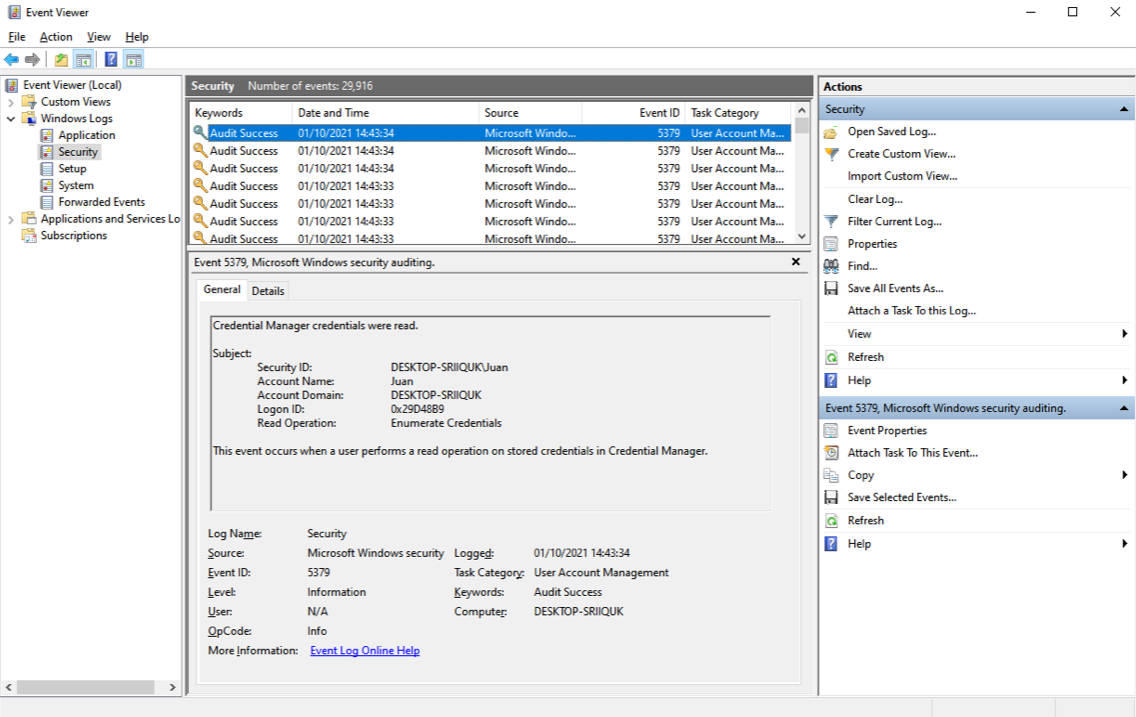
- https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/default.aspx
- https://resources.infosecinstitute.com/topic/6-windows-event-log-ids-to-monitor-now/
- https://www.lbmc.com/blog/top-11-windows-events-to-monitor/
- https://docs.google.com/spreadsheets/d/1BhR3cymZ53ZJfJdKAGKszuB-jgsr8GBJBOCJl50WGKE/edit#gid=326652879
Windows applications
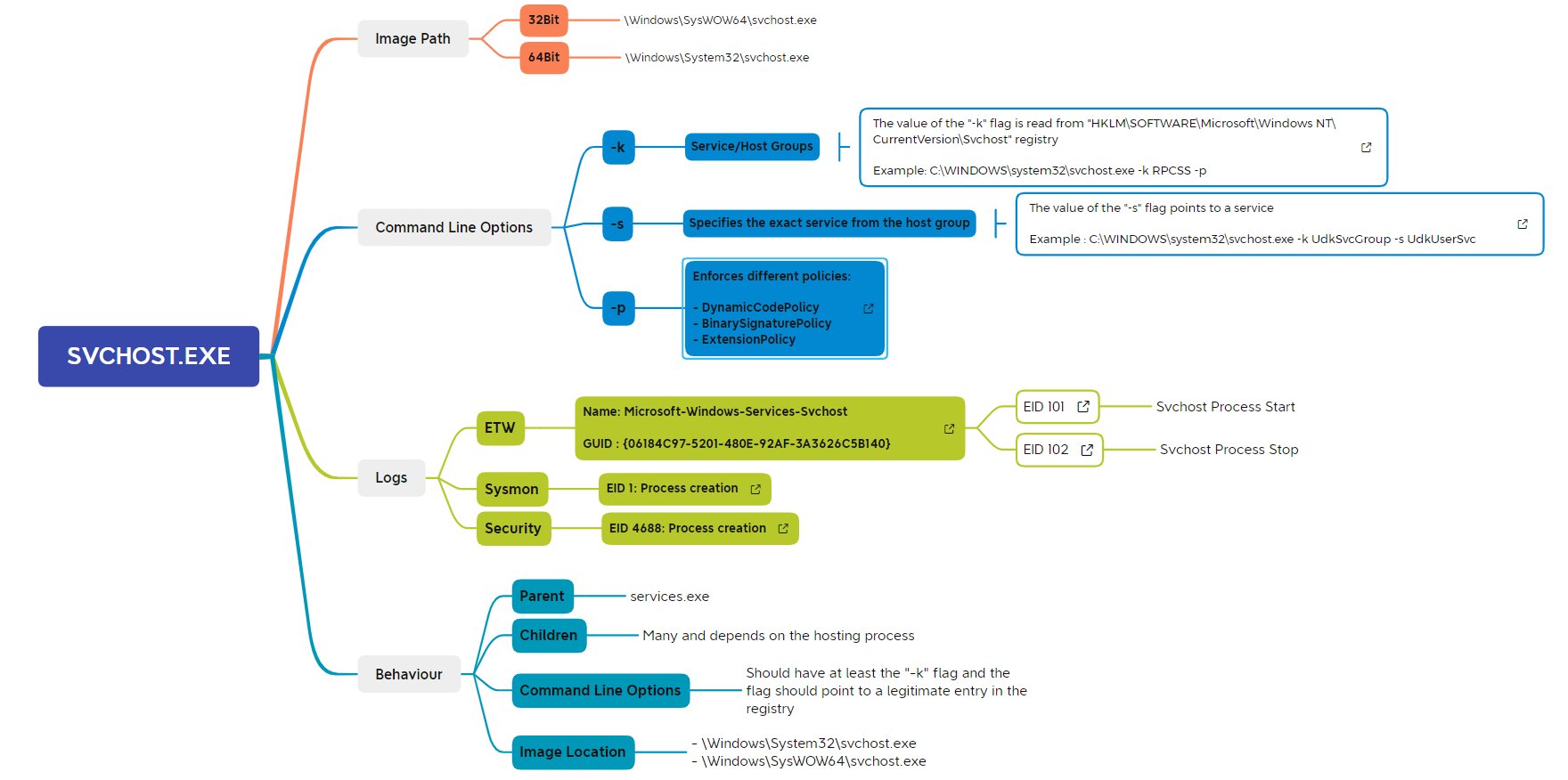
Sysmon
- A Windows system service and device driver for enhanced logs
- Not by default: must be installed explicitly
- Sysmon remains resident across system reboots to monitor and log system activity to the Windows event log
- Sysmon provides detailed information about process creations, network connections, and changes to file creation time
- Outputs wo windows event system (evtx)
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
https://github.com/SwiftOnSecurity/sysmon-config/blob/master/sysmonconfig-export.xml
- Logs process creation with full command line for both current and parent processes.
- Records the hash of process image files using SHA1 (the default), MD5, SHA256 or IMPHASH.
- Includes a process GUID in process create events to allow for correlation of events even when Windows reuses process IDs.
- Includes a session GUID in each event to allow correlation of events on same logon session.
- Logs loading of drivers or DLLs with their signatures and hashes.
- Logs opens for raw read access of disks and volumes.
- Logs network connections, including each connection’s source process, IP addresses, port numbers, hostnames and port names.
- Detects changes in file creation time to understand when a file was really created. - Rule filtering to include or exclude certain events dynamically.
Arguments against Sysmon:
- no support
- no central management
- extensive configs put the system under high load
- limited options to customize the output (format)
Osquery

Osquery exposes an OS as a relational database. This allows you to write SQL queries to explore operating system data. With osquery, SQL tables represent abstract concepts such as running processes, loaded kernel modules, open network connections, browser plugins, hardware events or file hashes.
Challenge
- You must get this data for all your devices
- This is a lot of data!
- Can we automate the process?
How to protect a Network?
- SIEM
- Endpoint detection and response (EDR)
- Intrusion Detection System (IDS)
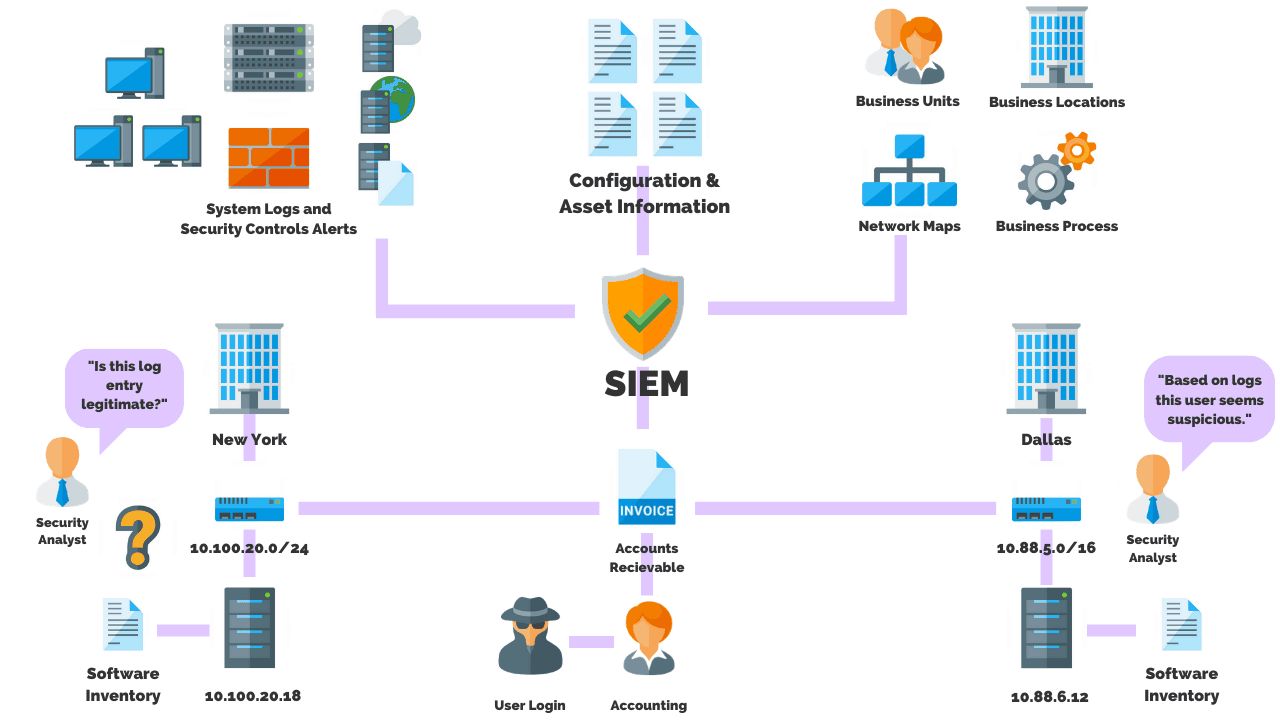
SIEM
A Security Information And Event Management (SIEM) solution supports threat detection, compliance and security incident management through the collection and analysis (both near real-time and historical) of security events, as well as a wide variety of other event and contextual data sources.
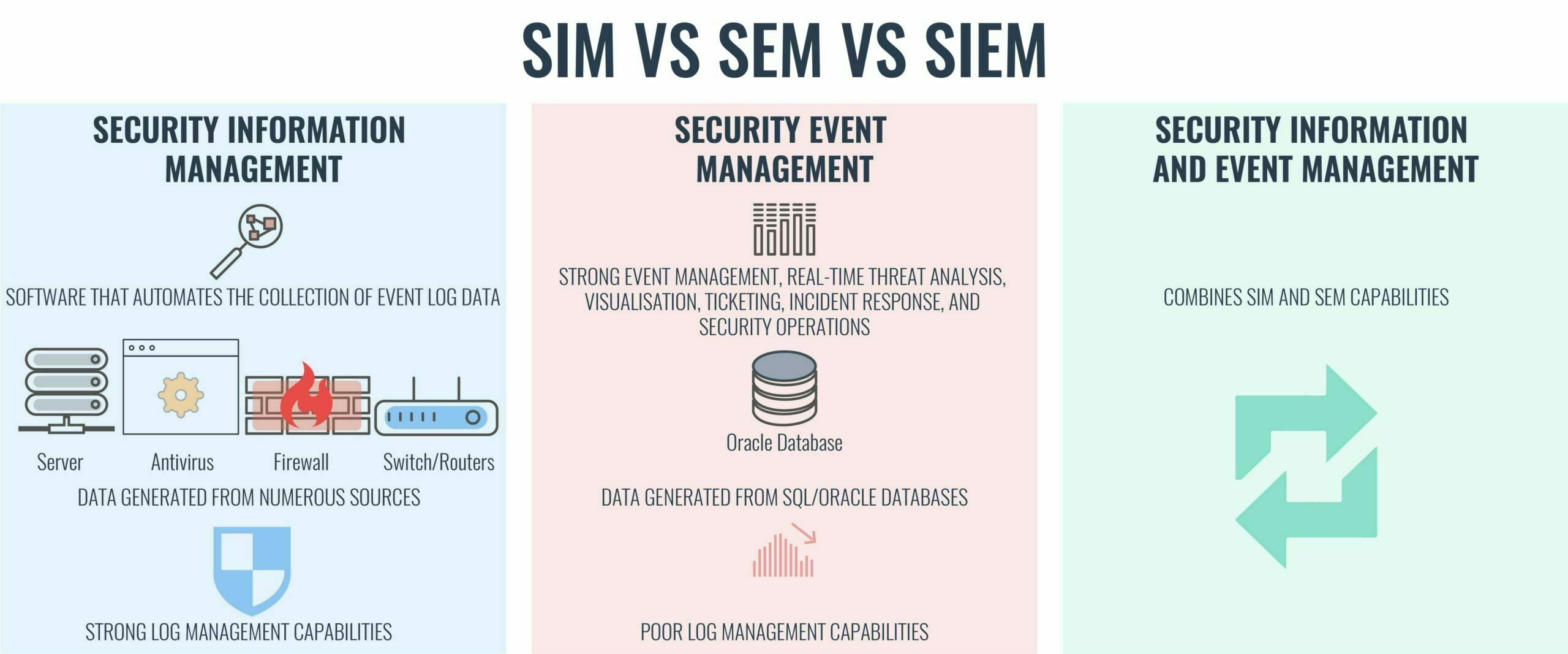
Architecture
Challenges
We already have a SIEM in our company. Is it not enough?
- Are you monitoring 100, 1000, or 10000 hosts?
- Do you have budget for commercial tools?
- How heterogeneous is your infrastructure?
- Are you just looking for security alerts, or do you also need persistent event logging for auditing purposes?
- Why do you get that many false positives/negatives? Are you investing time in customizing the alarms?
- What response time do you wish to achieve? Do you need real time notifications?
- Do you have time to improve/tune your solution or do you need something working 100% ASAP?
OS proposal
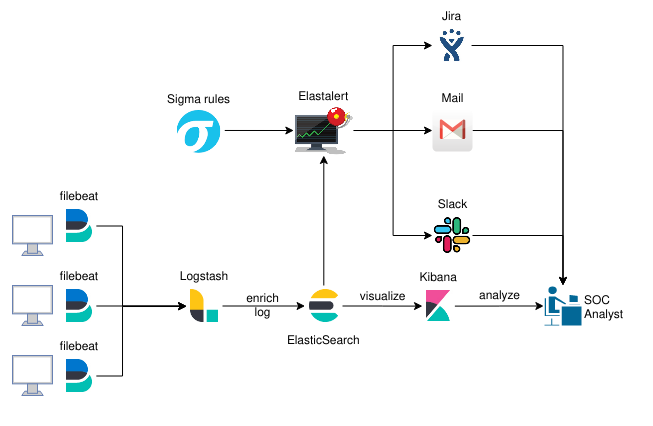
Wazuh
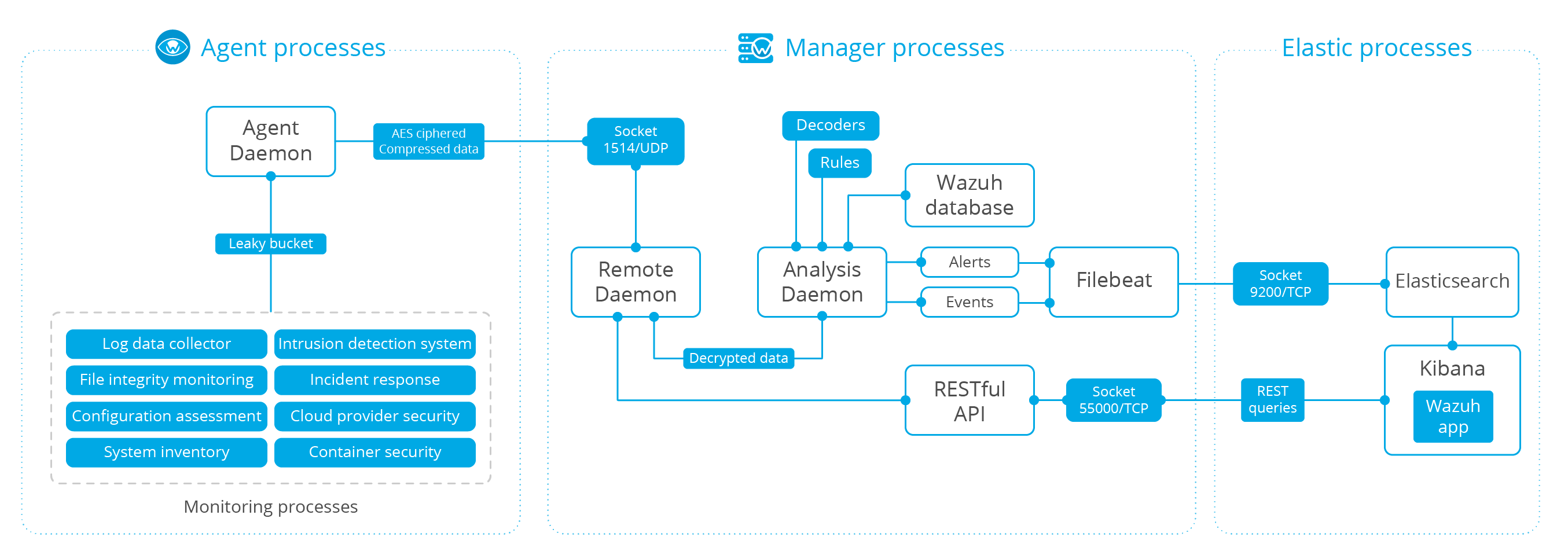


OS Examples
- Elastic: https://www.elastic.co/siem
- Elastalert: https://github.com/Yelp/elastalert
- HELK: https://github.com/Cyb3rWard0g/HELK
- Wazuh: https://wazuh.com/
Commercial examples
- QRadar
- Splunk
- Panda WatchGuard

Endpoint Protection and Response (EDR)
An EDR is a system that monitors (SIEM) and responds, either automatically or manually.
Features:
- Centralized server, gets events from all endpoints
- Manages IOCs and BIOCs (behavior indicators). Examples:
- executing apps from macros
- large uploads to servers
- antivirus
- Response: block an application, remove a IOC, isolate an endpoint
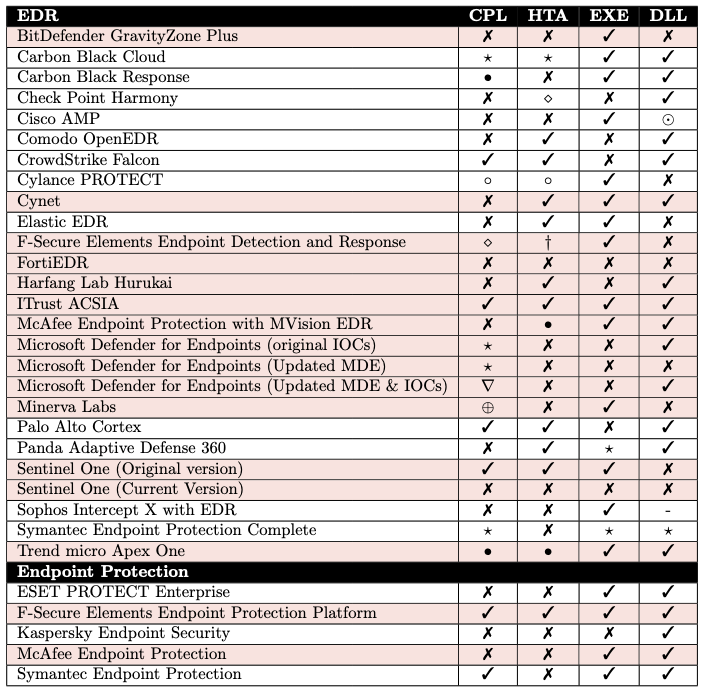
An Empirical Assessment of Endpoint Security Systems Against Advanced Persistent Threats Attack Vectors George Karantzas1 and Constantinos Patsakis, 2022. https://arxiv.org/pdf/2108.10422.pdf
Security Operations Center
SOC
A centralized team in a single organization that monitors the information technology environment for vulnerabilities, unauthorized activity, acceptable use/policy/procedure violations, intrusions into and out of the network, and provides direct support of the cyber incident response process.

SOC Services
Reactive:
- Monitoring and alerts
- Incident Response
- Forensics / eDiscovery
Proactive:
- Threat Hunting
- Health Monitoring
Trained personal
Highly skilled people can produce more accurate and timely results with a moderate product than novices with an expensive toolset.
Getting into the hunt
Assume that there is a likely compromise, become detection oriented and proactively mine data looking for patterns of intrusion and misbehaviour.
Define metrics
- Number of data sources
- MTT close an alarm
- Implemented Use Cases
- number of not-reviewed alerts after 24 hours
- ...
What makes good SOCs good
The SOC analyst
A day as a SOC analyst
- Alarm triage
- Dashboard review
- Review security state
- System health
- Active threat hunting
- Review intelligence data
Dashboard
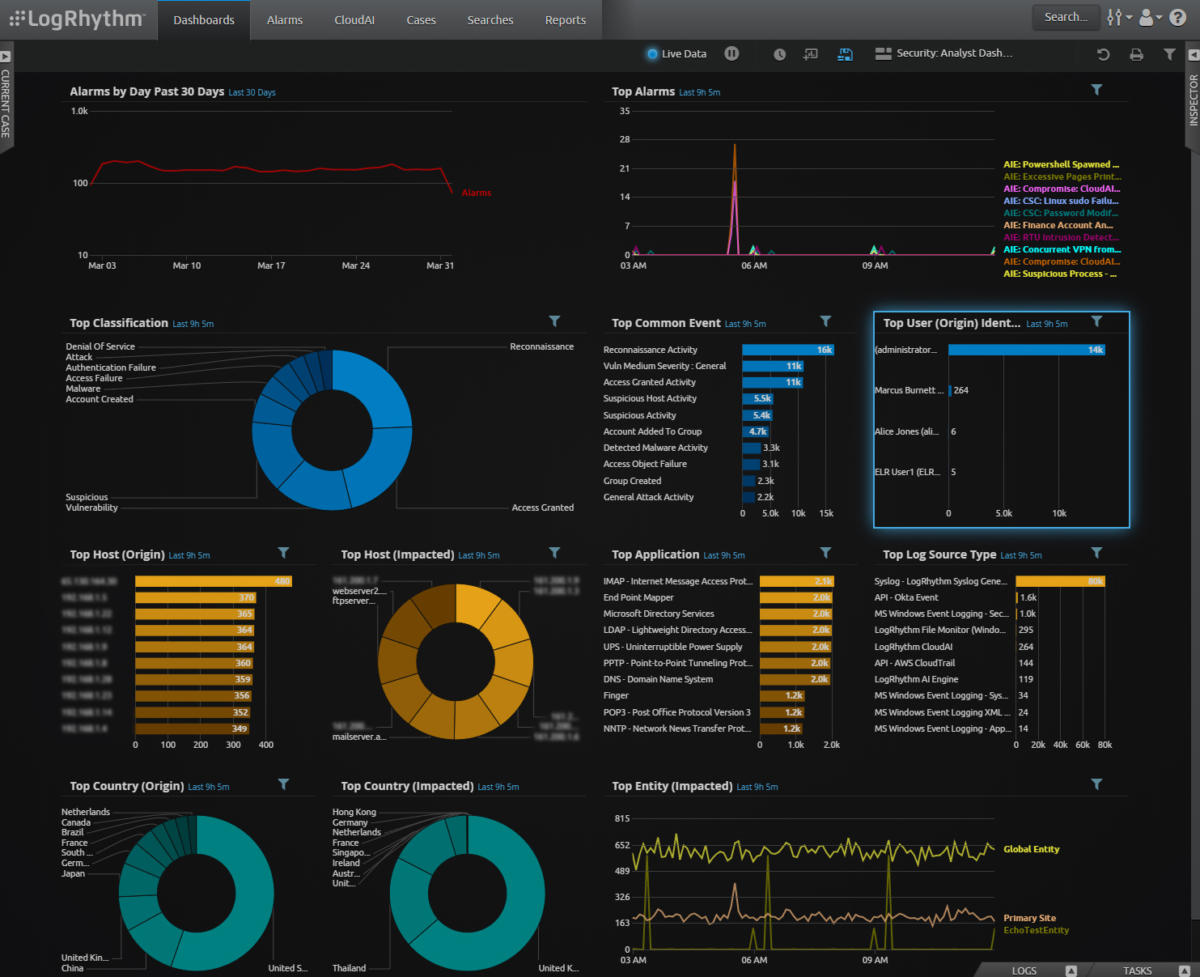
Indicators of Compromise (IoC)
An artifact observed on a network or in an operating system that, with high confidence, indicates a computer intrusion.
Yara rules:
Common Vulnerabilities and Exposures (CVE)
Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
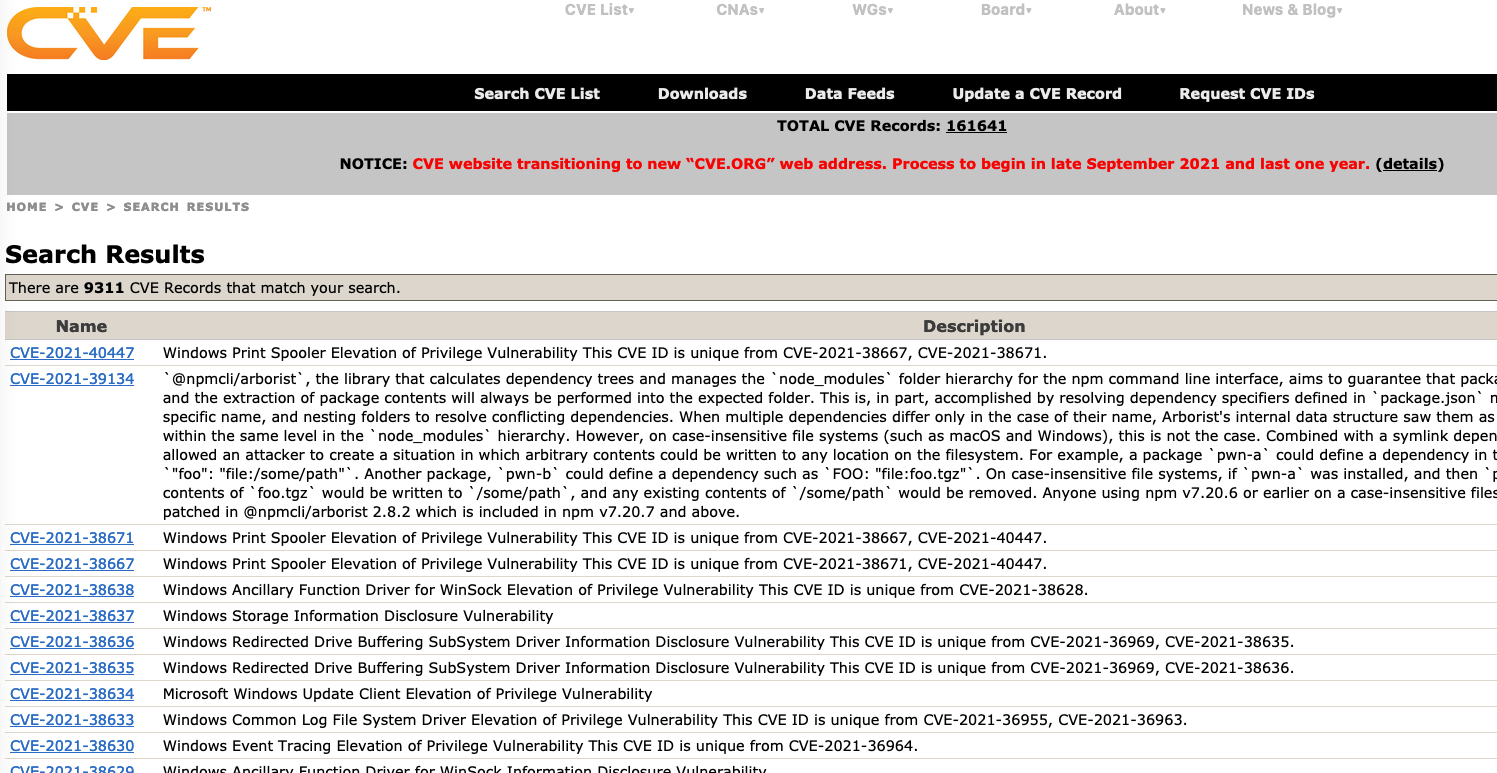
Reports
Playbooks
Remote forensics


Recommendations
Where do I start?
- MITRE ATT&CK® for Enterprise includes over 500 techniques and sub-techniques and the list grows with each release
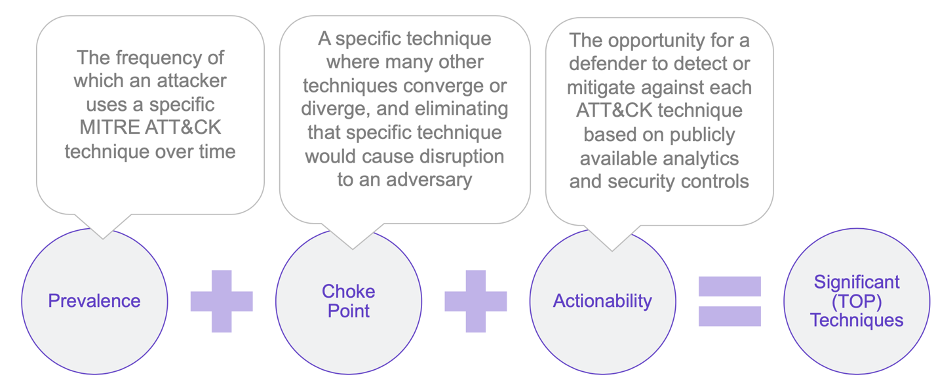
https://medium.com/mitre-engenuity/where-to-begin-prioritizing-att-ck-techniques-c535b50983f4
Mick Douglas (@bettersafetynet)
I've had 3 calls so far today (it's not even 10) about defending against Russian cyber ops. I'm tired of having the same call... so... here's what I've told everyone. This is the playbook you need... but it's not going to be what you think it will be. Ready? Lets go!
Feb 23, 2022
- Watch your egress. Firewalls work both ways. Carefully monitor outbound traffic. DMZ servers RESPOND to external requests. Look for DMZ systems initiating outbound. This is what "phoning home" (aka C2) looks like.
- you will have a handful of DMZ servers initiating outbound. File xfer systems, any mail server (you likely shouldn't be running your own). Some web services may also initiate outbound.
- Don't get too hung up on IP address blocks. Geo blocking has some advantages, but the only time Russian groups come from Russian IP space is when they want to rub it in. Start treating the entire internet as hostile... because it is.
- You 100% must know what is "normal" exes on your systems. App control (used to be call white listing) is no longer a "nice to have" it's IMO table stakes. Anyone who claims otherwise is giving dated & dangerous advice. Use native logging functions to know the apps that are running on systems.
- EDR
- Windows SRUM. It has a 30 day rolling view of EVERY exe run
- auditd or sysmon
- Because many orgs over rely on EDR and SIEM now, LOL attacks are highly successful. Attackers blend in. They are using core parts of the OS against you. None of your tools will stop these. You likely already have exclusions for the ports and protocols these tools use.
- Don't buy vendor tools to catch the attackers. No matter how good the demo is... it's a demo.
- If your IR plan doesn't have a rapid (host and network level) isolation workflows. Make it just after the stuff I've talked about in prior tweets. Drill it. You're going to need to work at a speed you likely haven't before.
- Increase your logging, while both filtering out stuff you don't care about at your aggregators, and SHORTENING the retention length for the data you don't need long term.
- The playbooks we've been following for too long are now being used against us. You can either accept that, or be beaten before you even show up to fight.
That said, you can win this fight. Once the attackers are in, you only need to detect them once. You can do stuff like make MSFT an untrusted publisher on a Windows box by allowing ONLY what is listed in SRUM analysis.
Your hosts tell you how they're being used and abused. Start listening. Prevent isn't possible. Try anyway. Move to a detect and respond model. That's our path to victory.
But it's rare.
Most orgs? Your exception list will fit on a single sheet of paper.
Hands on experience
Traffic-analysis.net
TBD
Build your own Lab
TBD